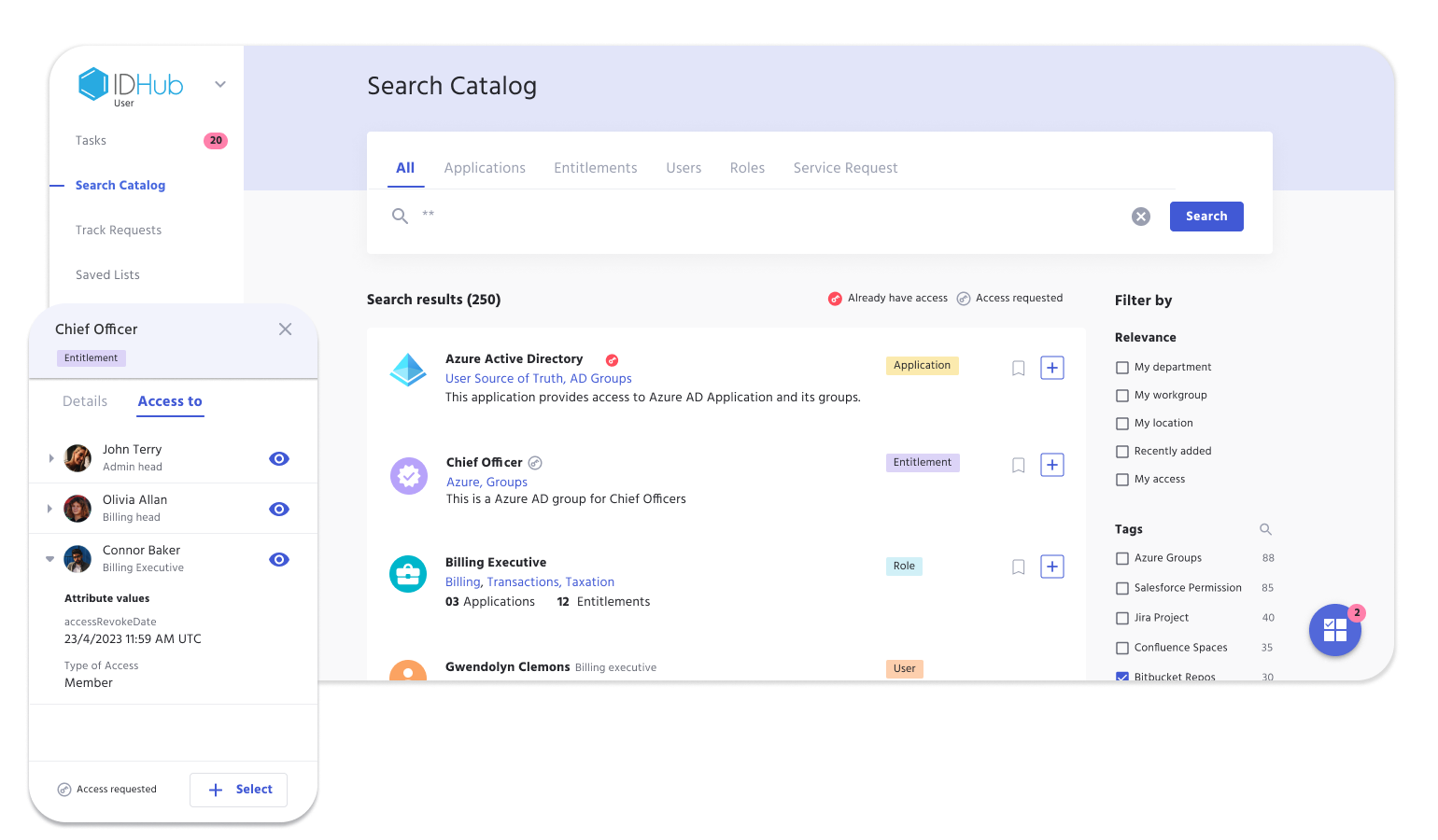
Secure Government Access
Public sector and critical infrastructure must secure against emerging cybersecurity threats by protecting access to sensitive data, applications, and systems. This requires a cybersecurity approach that includes strong identity governance.
Even with limited budgets and a shortage of trained cybersecurity personnel, government agencies can easily verify that user access is authorized, secure, and compliant. IDHub identity security is the foundation for digital modernization and helps organizations increase visibility, better manage digital identities, and reduce security threats.
What you can do:
- Automate the discovery, management, and control of all user access
- Migrate to the cloud with increased visibility across complex environments
- Advance zero trust with identity security to meet your mission
- Demonstrate proof of compliance with real-time access reports
Cyber Security Government
Government Digital Transformation
Meet Regulatory Compliance
IDHub supports compliance initiatives providing alignment with security and global compliance frameworks such as NIST and GDPR.
Ensure Zero Trust
Uphold your mission’s zero trust policies to enact least privilege access with a zero trust architecture leader.
Reduce Security Threats
Increase visibility into to all human, machine, and third-party access. Prevent over-provisioning and identify anomalous access.
Maintain Compliance
Ensure accurate audit readiness and maintain continuous compliance. Automate access reviews and approval processes.
Benefits of Digital Transformation in Government
Digital transformation empowers government agencies to operate more securely, efficiently, and in full compliance with evolving regulatory standards. By modernizing legacy systems and adopting identity-centric security practices, public sector organizations can:
Strengthen Regulatory Compliance
Automate access reviews, enforce least-privilege policies, and generate real-time audit reports to meet NIST, FISMA, and other federal requirements.
Improve Operational Efficiency
Replace manual access approvals and spreadsheets with streamlined workflows and automated provisioning to reduce human error and administrative burden.
Enhance Cyber Resilience
Gain visibility into who has access to what, across all systems, and quickly respond to threats with identity-based controls.
Support Cloud and Hybrid Environments
Securely manage user access as agencies migrate to the cloud, ensuring consistent policy enforcement across on-prem and cloud systems.
Enable Zero Trust Architecture
Implement strong identity governance to verify every user and device before granting access, a critical step toward meeting Zero Trust mandates.
With limited resources and increasing cyber threats, digital transformation, driven by secure identity and access management (IAM), helps agencies meet their mission while protecting public data and infrastructure.
Compliance Tools for Cyber Security
Cyber Security Tools
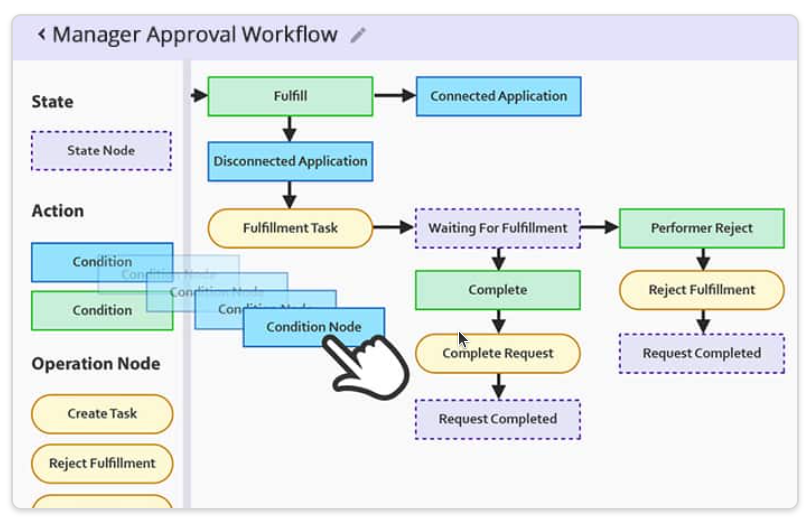
Customizable Approval Workflow Templates
Download our most common Workflow Templates, including editable versions in Visio, SVG, and PDF formats. Completely free to you.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.