IAM for Regulatory Compliance
With IDHub identity security, industries can automate access, ensure continuous regulatory compliance, and greatly reduce IT burdens. From government and education to financial services and healthcare, our solutions is designed for stringent, complex, regulated environments.
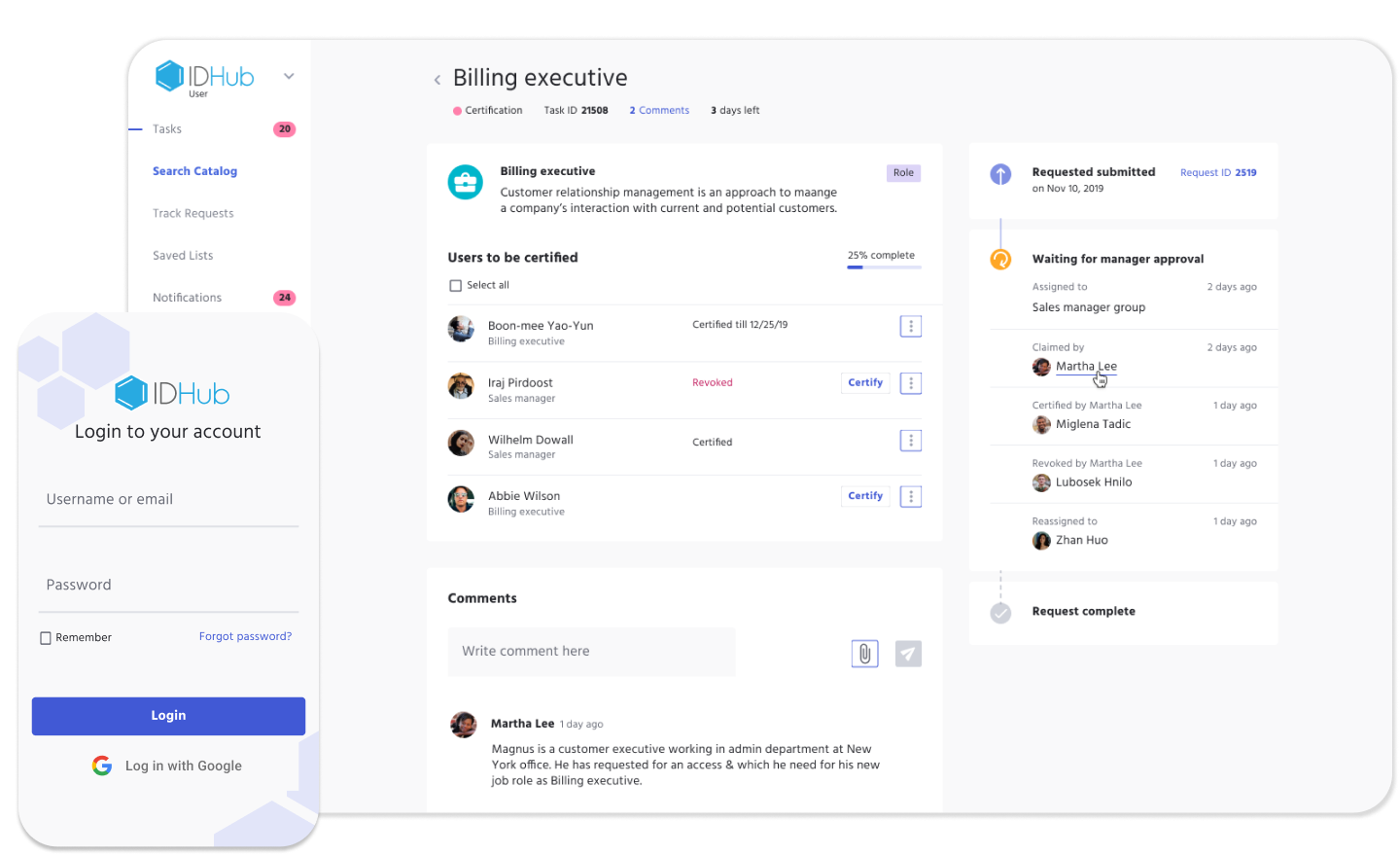
Identity and Access Management for Regulated Industries
Ensure Regulatory Compliance with IAM
Organizations across all industries face mounting challenges, from rising cyber threats and regulatory pressure to limited resources and the need to enable secure, efficient access for a dynamic workforce. Manual processes are no longer enough to manage identity at scale.
IDHub simplifies identity security by delivering the right access to the right users at the right time. With built-in automation powered by AI and machine learning, IDHub reduces operational costs, minimizes cyber risk, and ensures continuous compliance, keeping your organization secure and audit-ready.
Healthcare Compliance
Hospitals and healthcare providers must balance fast access to critical systems with strict security requirements. Manual identity management can't keep up with the complexity of shifting roles, multiple systems, and compliance demands.
Healthcare IAM simplifies access control, reduces security risks, and supports compliance for healthcare with regulations like HIPAA and HITECH—without slowing down care delivery.
Financial Services
Use identity and access management (IAM) to protect sensitive financial data, limit unauthorized access, and reduce the burden of manual processes. IAM helps financial institutions enforce access policies, maintain audit trails, and meet regulatory requirements with greater efficiency.
Learn how IAM supports Financial Service Compliance with regulations such as GLBA, SOX, and PCI DSS—while strengthening overall security.
Government Cyber Security
Meet and exceed your agency’s Identity, Credential, and Access Management (ICAM) objectives by improving visibility and securing access to government data no matter where it lives.
Learn more about how Identity and Access Management (IAM) solves Government Cyber Security Compliance.
Manufacturing Cyber Security
Advance your manufacturing cyber security technologies with confidence through intelligent identity security. Control access for human, non-human, and third-parties.
Higher Education
Modernize your higher education IT with intelligent identity security. Give faculty, staff, and students quick, secure access to applications and files while protecting sensitive data.
Utilites & Energy
Provide the visibility and intelligence you need to manage and control access to critical infrastructure and protect sensitive energy information.
Reduce risk with our fast identity security to automatically detect and remediate risky access across all applications, data, and platforms.
Meet and exceed your agency’s SOX and FERC compliance by improving visibility and control of all access to important data no matter where it lives.
Compliance Tools for Cyber Security
Cyber Security Tools
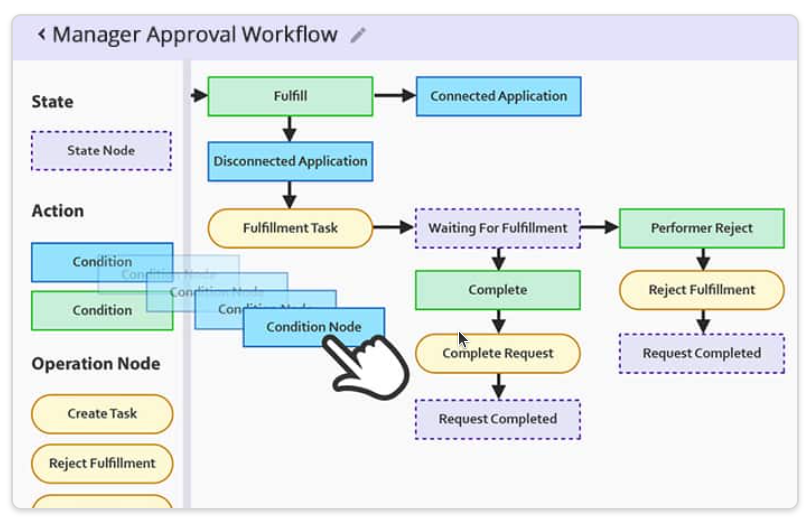
Customizable Approval Workflow Templates
Download our most common Workflow Templates, including editable versions in Visio, SVG, and PDF formats. Completely free to you.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.